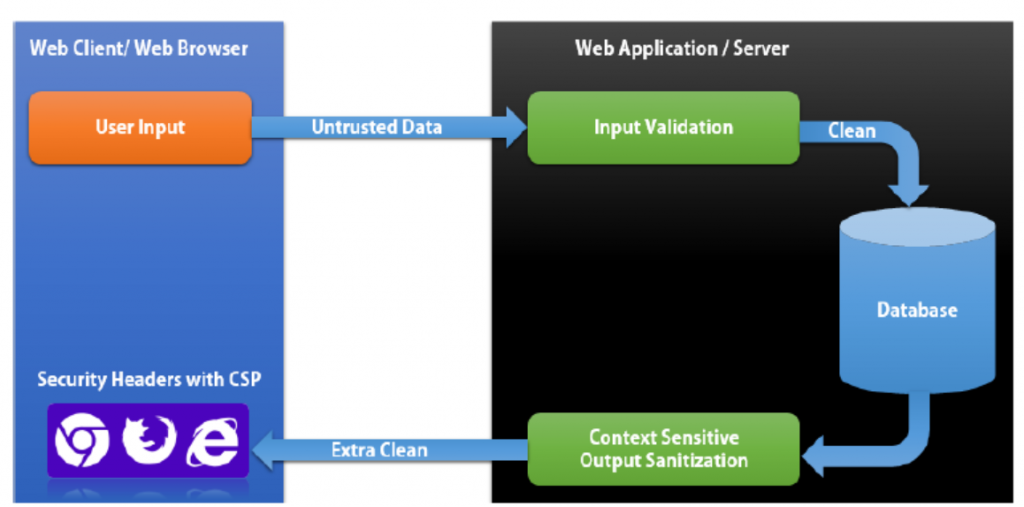
Web Security 免費測試工具與相關資源

這篇文章主要介紹幾種測試Web Security Testing 與 XSS 的工具,
最後說明XSS防護方法與相關資源。
哪一種工具最好用?
其實自己習慣,團隊可以熟悉應用在安全開發測試流程中就是最好用。
7+ XSS免費測試工具
Xenotix XSS Exploit Framework
- OWASP Xenotix XSS Exploit Framework http://xenotix.in/

IronWASP
- IronWASP https://ironwasp.org/download.html

arachni

ImmuniWeb Self-Fuzzer Addon for Firefox
- ImmuniWeb Self-Fuzzer Addon for Firefox https://addons.mozilla.org/en-US/firefox/addon/immuniweb-self-fuzzer/

VEGA

OWASP ZAP

BurpSuite

Xenotix XSS相關文件與教學
https://www.owasp.org/index.php/OWASP_Xenotix_XSS_Exploit_Framework
XSS 防護之道 – 編碼
http://www.strictly-software.com/scripts/downloads/encoder.js
http://www.strictly-software.com/htmlencode
- 將使用者輸入資料做一定的驗證
- 資料儲存到資料庫前編碼
- 資料輸出到瀏覽器執行前編碼
HTML 編碼
[pastacode lang=”markup” message=”” highlight=”” provider=”manual”]
<h1> Welcome html_escape(untrusted string) </html>[/pastacode]
編碼的用意在於轉換下列符號,讓輸入的資料不會變成任意執行的JavaScript 程式碼
| & | & |
| < | < |
| > | > |
| “ | " |
| ` | ` |
| ‘ | ' |
| / | / |
編碼HTML中的屬性
[pastacode lang=”markup” message=”” highlight=”” provider=”manual”]
<img src="x" alt="html_escape(untrusted string)">[/pastacode]
編碼URL
<a href=”http://sampleWebsite.com/index?test=url_escape(untrusted string)“>l</a>
黑名單或是白名單的資料驗證?
如果可以建議使用白名單。只允許特定字元輸入。
善用HTML tag
明確定義UTF8文件編碼:
- <meta http–equiv=”content-type” content=”text/html;charset=UTF-8“>
在<html>前定義
- <!doctype html>
使用HTTP Header定義
這些 Http Header 定義可以讓瀏覽器也啟動內建 XSS保護機制,相關的 Http header 如下:
- X-XSS-Protection: 1; mode=block
- X-Frame-Options: deny
- X-Content-Type-Options: nosniff
- Content-Security-Policy: default-src ‘self’
- Set-Cookie: key=value; HttpOnly
- Content-Type: type/subtype; charset=utf-8
JavaScript程式如何防護呢?
http://www.strictly-software.com/htmlencode
http://www.strictly-software.com/scripts/downloads/encoder.js
- HTML2Numerical
- numEncode
- htmlEncode
- XSSEncode
- correctEncoding
- stripUnicode
如果是 jQuery 可以使用 .text() 而不是 .html()
相關資源
當然每一種 UI framework 或是網頁開發程式語言都會提供相關的 HTML encoding 的工具與函數
https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet
https://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet
https://www.owasp.org/index.php/List_of_useful_HTTP_headers
https://www.owasp.org/index.php/HttpOnly
https://www.owasp.org/index.php/OWASP_Xenotix_XSS_Exploit_Framework https://www.owasp.org/index.php/OWASP_Java_Encoder_Project
https://code.google.com/p/owasp-esapi-java/
http://www.w3.org/TR/CSP11/
https://w3c.github.io/webappsec/specs/content-security-policy/
http://www.html5rocks.com/en/tutorials/security/content-security-policy/
https://tools.ietf.org/rfc/rfc7034.txt
http://msdn.microsoft.com/en-us/library/system.web.security.antixss.antixssencoder(v=vs.110).aspx
http://msdn.microsoft.com/en-us/library/system.web.httputility(v=vs.110).aspx
http://openmya.hacker.jp/hasegawa/security/utf7cs.html
http://www.thespanner.co.uk/2013/05/16/dom-clobbering/
http://www.slideshare.net/x00mario/the-innerhtml-apocalypse/46
http://wpl.codeplex.com/ http://opensecurity.in/
http://cure53.de/fp170.pdf
https://www.modsecurity.org/
https://www.ironbee.com/
http://taligarsiel.com/Projects/howbrowserswork1.htm
https://frederik-braun.com/xfo-clickjacking.pdf
http://mootools.net/docs/core/Types/String
http://www.strictly-software.com/htmlencode
http://backbonejs.org/#Model
https://www.ng-book.com/p/Security/
https://docs.angularjs.org/api/ng/service/$sce
http://spinejs.com/docs/views
https://github.com/cure53/DOMPurify
https://github.com/leizongmin/js-xss
http://api.rubyonrails.org/classes/ERB/Util.html
http://api.rubyonrails.org/classes/ActionView/Helpers/SanitizeHelper.html
http://yuilibrary.com/yui/docs/api/classes/Escape.html#method_html
http://prototypejs.org/doc/latest/language/String/prototype/escapeHTML/
http://docs.php.net/manual/en/function.htmlspecialchars.php
http://www.smarty.net/docsv2/en/language.modifier.escape
https://www.superevr.com/blog/2012/exploiting-xss-in-ajax-web-applications/
http://blog.opensecurityresearch.com/2011/12/evading-content-security-policy-with.html
http://www.janoszen.com/2012/04/16/proper-xss-protection-in-javascript-php-and-smarty/
http://wpcme.coverity.com/wp-content/uploads/What_Every_Developer_Should_Know_0213.pdf