防禦DDOS的Web services安全設計建議

這篇文章主要對於 Web Services 防護 DDOS的安全設計提出建議
DDOS 攻擊的類型
攻擊者利用許多被控制的電腦 (BOTS)對特定受害服務器發起大量的請求
造成受害者服務暨服務癱瘓所造成的攻擊, 簡稱 DDOS (Distributed Denial of Service)
常見的 DDOS攻擊分類如下:
將 DDOS攻擊分類的主要原因是因為每種不同的攻擊會有不同的防護方案
網路基礎層攻擊
TCP Syn Flood與 User Datagram Protocol (UDP) reflection是最常見的攻擊方式
藉由傳送大量的網絡封包造成目標受害者電腦癱瘓, 這樣的攻擊行為通常可以透過防火牆或是IPS識別
另外,基於UDP協議的攻擊有 Domain Name System (DNS), Network Time Protocol (NTP), 與 Simple Service Discovery Protocol (SSDP)等, 這些攻擊善用受害者伺服器會回覆固定大小的封包造成網絡癱瘓
應用層攻擊
應用層的攻擊主要針對Web服務器, 多半基於HTTP協議的攻擊
- HTTP Slow Attack: 讓伺服器等待每一個連結請求, 最終導致伺服器無法服務其他請求
- HTTP Flood: 大量的 HTTP請求造成Web伺服器癱瘓
- SSL renegotiation Attack: 透過大量SSL重協商造成伺服器癱瘓
實務上常見的DDOS攻擊, 可能結合上述網絡層與應用層的攻擊, 防護方式介紹如下:
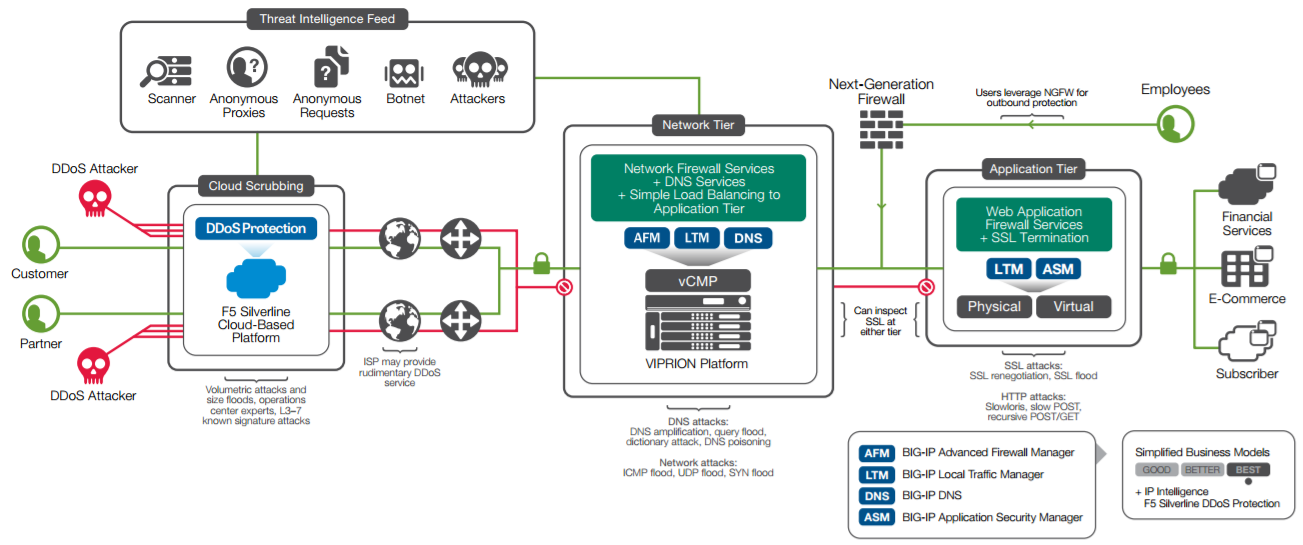
多層次的防護
整體來說DDOS的防護可分為三大層次
- 網絡近源清洗
- 網路層過濾
- 應用層過濾
Web服務防護設定建議
一般來說 Web sercvices 都會有設定連線時間與數量等相關設定, 舉nginX例子如下:
特別要提醒的是這樣的方法只能有部分的防禦效果, 還是必須靠網路流量清洗才可以完整的防禦.
Mitigating Slow HTTP DoS Attack
## Timeouts definition ## client_body_timeout 10; client_header_timeout 10; keepalive_timeout 5 5; send_timeout 10; ## End ##
- client_body_timeout: Defines a timeout for reading client request body. The timeout is set only for a period between two successive read operations, not for the transmission of the whole request body. If a client does not transmit anything within this time, the 408 (Request Time-out) error is returned to the client.
- client_header_timeout: Defines a timeout for reading client request header. If a client does not transmit the entire header within this time, the 408 (Request Time-out) error is returned to the client.
- keepalive_timeout: The first parameter sets a timeout during which a keep-alive client connection will stay open on the server side. The zero value disables keep-alive client connections. The optional second parameter sets a value in the “Keep-Alive: timeout=time” response header field. Two parameters may differ. The “Keep-Alive: timeout=time” header field is recognized by Mozilla and Konqueror. MSIE closes keep-alive connections by itself in about 60 seconds.
- send_timeout: Sets a timeout for transmitting a response to the client. The timeout is set only between two successive write operations, not for the transmission of the whole response. If the client does not receive anything within this time, the connection is closed.
參考
SEC307 – Building a DDoS-Resilient Architecture with AWS
SEC306 – Defending Against DDoS Attacks
https://code.google.com/p/slowhttptest/